An Overview of Single Sign On (SSO)

Single sign-on (SSO) is a user and session service that enables users to login with one set of credentials, for example their username and password. This allows them to access more than one application with just one menu. SSO can be used by enterprises, smaller organizations and individuals in order to develop ease of management when it comes to user authentication.
With a basic web SSO service, an agent module on the application server retrieves specific authentication credentials for each individual user from a dedicated SSO policy server. The credential retrieval happens when authenticating the user against their personal database – such as an LDAP (Lightweight Directory Access Protocol) directory- and then authenticates them to all of their other applications in one session! This also eliminates any future password prompts for applications during that session.
How single sign-on works
Single sign-on is, essentially, a federated identity management (FIM) system, and the use of said system is sometimes referred to as identity federation. O-Auth, which is an abbreviation for Open Authorization, is the framework that allows an end user’s account information to be safely used by third party services or applications like Instagram and Facebook, without exposing their password.
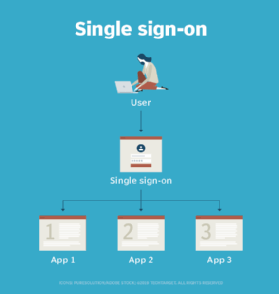 This visualization shows how single sign-on works
This visualization shows how single sign-on works
O-Auth serves as an intermediary on behalf of an end user by providing the service or application with an access token that grants the authority to share their specific account information.
Types of SSO configurations
Certain SSO services utilize protocols, like Security Assertion Markup Language (SAML) and Kerberos.
- SAML is an extensible markup language (XML) standard that facilitates the secure exchange of user authorization and authentication data across domains. SSO services that utilize SAML involve communications between the user, an identity provider (one that maintains a user directory) and a service provider.
- Kerberos is a network authentication protocol that reduces the risk of eavesdropping and replay attacks. It is a network service for granting tickets to access resources, instead of sharing passwords or keys between different services. In a Kerberos-based set up, when the user enters their credentials, a ticket granting ticket (TGT) is generated. This TGT then fetches service tickets for various apps the user wants to access, without asking the user to re-enter their credentials.
- SSO services using smart cards will ask the end user to enter the sign-in credentials on the card for the initial login. From then on, the user won’t have to re-enter usernames and passwords. SSO smart cards either store passwords or certificates.
SSO and Security
Although Single Sign-On is convenient for users, it also presents risks to enterprise security. A hacker who gains access to a user’s SSO credentials will be granted access to every application that the user has rights to, increasing the potential mayhem that will ensue. To prevent malicious actors from gaining access, it’s essential that each aspect of SSO implementation is coupled with identity governance. Most organizations use two-factor authentication (2FA) or multifactor authentication (MFA) in unison with SSO to ensure optimal security.
Social SSO
Facebook, Google and LinkedIn are platforms offering popular SSO services that enable end users to login to third-party applications with only their social media credentials. Despite creating more convenience for users, Social SSO may be more of a liability as it creates a single point of failure that can easily be exploited by malicious actors.
End users should be aware that if they use social SSO services, and an attacker gains control over their credentials then the attacker will have access to all of their online accounts. This could lead to identity or money being stolen so it’s advised not to take any chances by using a more secure authentication service like 2FA.
Apple has announced the release of their own single sign-on service, i.e., Sign in with Apple. This will be a more private alternative to other SSO options by Google and Facebook that have been revealed recently. The new product is expected to limit what data third party services can access while also enhancing security measures for iOS users through 2FA requirements on all accounts linked up via Face ID or Touch ID.
Enterprise SSO
Enterprise Single Sign On (eSSO) software and services work as password managers with client and server components; they log the user onto target applications by repeating user credentials. These credentials almost always consist of a username and password, and target applications that don’t usually require any modifications for seamless integration with the eSSO system.
Advantages and Disadvantages of SSO
Some advantages of Single Sign On include:
- Users don’t have to worry about remembering or storing a plethora of usernames and passwords for each application they log on to.
- SSO reduces the time it takes for employees to sign in and get to work, thereby increasing productivity and improving workflows.
- SSO helps combat and mitigate phishing.
- SSO makes password management a breeze, resulting in fewer roadblocks for employees.
Some disadvantages of Single Sign On include:
- SSO doesn’t provide additional security checks that certain application sign-ons may require.
- If you lose availability, then everyone will be locked out of the multiple applications and systems connected to the SSO service.
- If a hacker or malicious actors gain access, they’ll be able to access all the applications and systems connected to SSO.
SSO vendors
Some of the most well-known and popular SSO vendors include:
- Rippling, which enables end users to sign onto cloud applications from various devices.
- Avatier Identity Anywhere is an SSO service for Docker, container-based platforms.
- OneLogin is an identity and access management (IAM) platform based in the cloud that supports SSO.
- Okta is a popular tool that supports SSO. Most enterprise users opt for Okta as it supports 2FA (two factor authentication) and is more secure than its alternatives.
Conclusion
Single sign-on (SSO) is a way for users to authenticate themselves to multiple systems with one set of credentials. SSO has many benefits, but can also pose some security risks if not implemented correctly.
Mpire Solutions offers a variety of services including social and enterprise SSO solutions that will make it easy for you to integrate the technology into your existing infrastructure without compromising on data protection standards or user experience. For more information about our offerings, reach out to us today!




